Proxies, Reverse Proxies, and Load Balancers: The Backbone of Modern Networking
Proxies and reverse proxies play an important role in connecting users (clients) with servers. They help handle requests, improve speed, add security, and make systems more reliable. When used with tools like load balancers, they make websites and apps work better, even during heavy traffic.
In this blog, we’ll break down what proxies, reverse proxies, and load balancers are, how they work, and why they are useful—using simple terms everyone can understand.
What Is a Proxy?
A proxy is like a middleman between your device (the client) and the website or service you want to access. Instead of your device talking directly to the website, the proxy talks to the website for you.
How It Works:
- Your device connects to the proxy.
- The proxy sends your request (like opening a website) to the destination.
- The website only sees the proxy’s information, not yours.
Why Use a Proxy?
- Stay Private
- What It Means: When you browse the internet, your device’s IP address is visible to the websites you visit. This IP address reveals your approximate location and sometimes other identifying details.
- How a Proxy Helps: Instead of exposing your IP address, the proxy’s IP address is shown to the website. This makes it harder for websites or other entities to track you directly.
- Example: If you’re browsing from India but use a proxy server located in the US, the website will think your request is coming from the US.
- Faster Browsing
- What It Means: When a proxy server stores a copy of frequently visited websites (a process called caching), it can serve you that copy instead of fetching it again from the internet.
- How It Works:
- If multiple people or devices are accessing the same content (e.g., a company’s employees visiting the same news site), the proxy saves time by delivering the stored version.
- This reduces load on the original website and speeds up access for users.
- Example: You open a news website daily. If the proxy has already cached yesterday’s articles, it can load those instantly without fetching them again.
- Monitoring and Debugging
- What It Means: Developers and IT teams often use proxies to inspect or debug network traffic.
- How It Works:
- A proxy can capture data from your requests and responses, showing what’s being sent and received. This is especially useful for:
- Troubleshooting application errors. Checking if requests are secure or contain sensitive information.
- Example: A developer uses tools like Fiddler (a type of proxy) to monitor an app’s network requests and ensure they are reaching the correct server.
- Blocking Content
- What It Means: Organizations and schools often use proxies to control what users can access on the internet.
- How It Works:
- The proxy checks every website request against a list of allowed or blocked sites.
- If the website is on the blocked list, the proxy denies access.
- Example: A company might block access to social media sites like Facebook during work hours using a proxy.
What Is a Reverse Proxy?
A reverse proxy does the opposite of a regular proxy. Instead of helping the client, it works on behalf of the server. It sits in front of servers and handles incoming requests.
How It Works:
- You send your request to a reverse proxy (e.g., Google.com).
- The reverse proxy forwards your request to one of the backend servers.
- The server sends a response back to the reverse proxy, which then sends it to you.
Why Use a Reverse Proxy?
-
Distribute Work (Load Balancing)
- What It Means: If a website or application has many visitors, sending all traffic to one server can overwhelm it, causing delays or crashes. A reverse proxy helps by spreading the workload across multiple servers.
- How It Works:
- When a user sends a request, the reverse proxy decides which backend server to send it to.
- It can use various methods like:
- Round Robin: Alternates requests between servers.
- Least Connections: Sends the request to the server handling the fewest connections.
- Custom Rules: Routes based on workload or other factors.
- Example: A popular e-commerce site uses three servers to handle incoming orders. The reverse proxy ensures no single server gets overloaded by distributing the traffic evenly.
-
Speed Up Responses (Caching)
- What It Means: A reverse proxy can store (or cache) copies of frequently accessed content, like images, videos, or static web pages. This allows the proxy to serve the cached content directly, without contacting the backend servers every time.
- How It Works:
- When a user requests a webpage, the reverse proxy checks if it has a cached version.
- If available, it serves the cached version, saving time.
- If not, it forwards the request to the backend server and stores the response for future use.
- Example: A news website with high traffic stores copies of its homepage. When users access the site, the reverse proxy serves the cached page, speeding up the response time and reducing the load on backend servers.
-
Extra Security
- What It Means: Reverse proxies act as a shield for backend servers, hiding their details (like IP addresses) from clients and protecting them from direct attacks.
- How It Works:
- The reverse proxy acts as the only visible point to the client.
- Attackers targeting the system will hit the reverse proxy, not the actual backend servers.
- Security features like firewalls, request filtering, and DDoS protection can be added to the reverse proxy for enhanced protection.
- Example: In a banking app, the reverse proxy ensures that the backend servers handling sensitive data are hidden and protected, making it harder for hackers to target them.
-
Smart Routing
- What It Means: The reverse proxy can route different types of requests to different backend servers based on predefined rules.
- How It Works:
- The reverse proxy analyzes each request to determine its type or destination.
- It sends the request to the most suitable server.
- Example:
- Scenario 1: Requests for images are sent to a server optimized for handling large media files.
- Scenario 2: API requests are routed to a server designed for processing data-heavy operations.
Proxy vs. Reverse Proxy: Key Differences
| Feature | Proxy | Reverse Proxy |
|---|---|---|
| Client Interaction | Knows the server's final destination | Does not know the backend server |
| Server Visibility | Cannot identify the client | Knows the client |
| Primary Use | Anonymity, caching, monitoring | Load balancing, routing, security |
Load Balancers: Dividing Work Between Servers
Load balancers are reverse proxies with extra features. They divide traffic between multiple servers to keep things running smoothly.
There are two types:
- Layer 4 load balancers (Transport layer)
- Layer 7 proxy balancers (Applications layer)
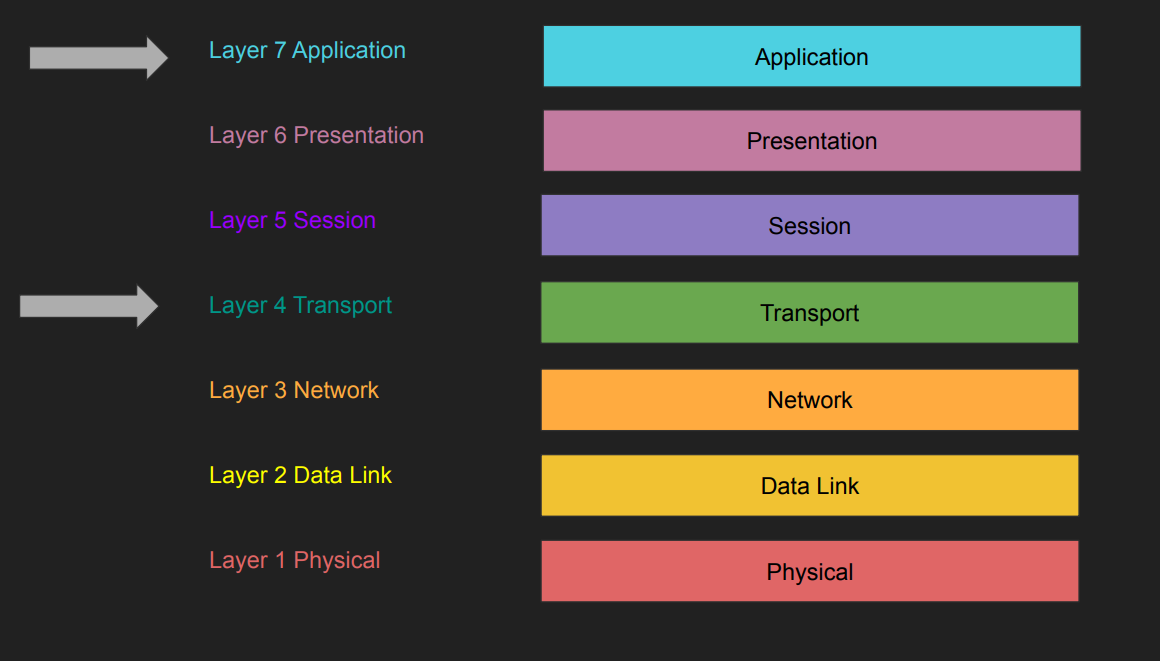
Layer 4 load balancers
A Layer 4 Load Balancer operates at the transport layer of the OSI model. This means it handles traffic at the connection level using information like IP addresses and port numbers, without inspecting or processing the actual data being sent.
How It Works
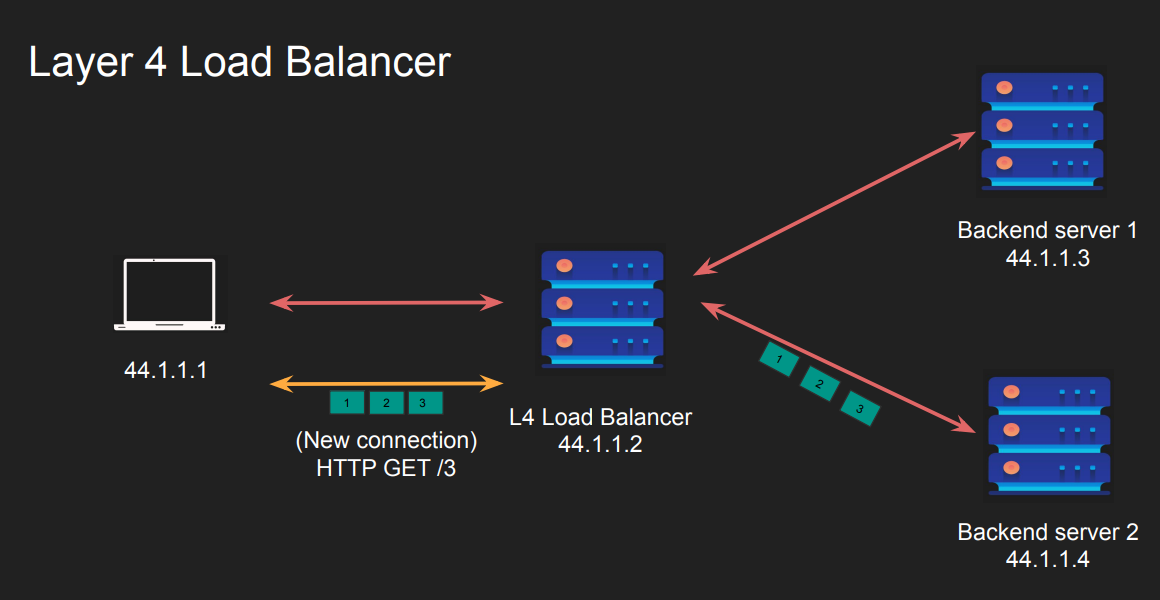
-
Connection Handling:
When a client sends a request, the Layer 4 load balancer:- Receives the request and checks the client’s IP address and port.
- Matches the request with a backend server from a pool of servers based on predefined rules (e.g., round robin or least connections).
- Establishes a TCP (or UDP) connection with the selected backend server.
- Forwards all packets from the client to that server, treating them as raw data.
-
No Content Awareness:
The Layer 4 load balancer does not inspect the content of the data packets. It simply forwards them as they are. -
Session Persistence:
A Layer 4 load balancer ensures that all packets in a session are sent to the same backend server. This is important because:- Splitting packets from a single session across multiple servers can cause data corruption.
- To maintain consistency, the load balancer keeps track of active client-server connections.
Pros of Layer 4 Load Balancers
-
Fast and Simple:
- Layer 4 load balancers handle data at the connection level, avoiding the overhead of inspecting or processing application-layer data.
- They are highly efficient, with minimal latency.
-
Protocol-Agnostic:
- Since they work with raw TCP or UDP packets, Layer 4 load balancers support virtually any protocol (e.g., HTTP, FTP, WebSocket, gRPC, etc.).
- This flexibility makes them suitable for diverse use cases, including streaming, file transfer, and real-time applications.
-
Low Resource Usage:
- They don’t need to buffer or analyze data, resulting in lower CPU and memory usage compared to Layer 7 load balancers.
Cons of Layer 4 Load Balancers
-
Limited Intelligence:
- Layer 4 load balancers cannot make decisions based on the content of requests, such as routing based on API paths or user data.
- Example: They cannot differentiate between requests for
/imagesand/videosto route them to specialized servers.
-
No Caching:
- Without content inspection, Layer 4 load balancers cannot store and serve frequently accessed content.
- This results in higher load on backend servers, especially for static resources like images or files.
-
Sticky Sessions Only:
- Once a session is assigned to a server, all packets for that session must go to the same server. This can lead to uneven load distribution if some sessions are much heavier than others.
-
Less Suitable for Microservices:
- Microservices often require intelligent routing based on application-layer data (e.g., headers, URLs). Layer 4 load balancers lack the ability to process this information.
Example Use Case for Layer 4 Load Balancer
Streaming Applications:
- For video streaming platforms, the content does not need to be inspected, as the focus is on fast and reliable delivery of data.
- A Layer 4 load balancer efficiently distributes traffic between multiple servers without adding unnecessary overhead.
When to Choose Layer 4 Load Balancers
- High-Speed Applications: When speed and low latency are critical.
- Protocol Flexibility: When your application uses diverse or custom protocols.
- Simplicity: When basic traffic distribution is sufficient, and advanced features like content-based routing or caching are not required.
Layer 4 load balancers are perfect for scenarios that prioritize performance and efficiency over advanced routing logic. However, for more complex requirements like handling API requests or implementing microservices, Layer 7 load balancers are a better fit.
Layer 7 load balancers
A Layer 7 Load Balancer operates at the application layer of the OSI model. Unlike Layer 4 load balancers, which only look at connection-level details like IP addresses and ports, a Layer 7 load balancer inspects the actual content of network requests, such as URLs, headers, or even the body of HTTP requests. This enables it to make smarter and more specific decisions about how to route traffic.
How It Works
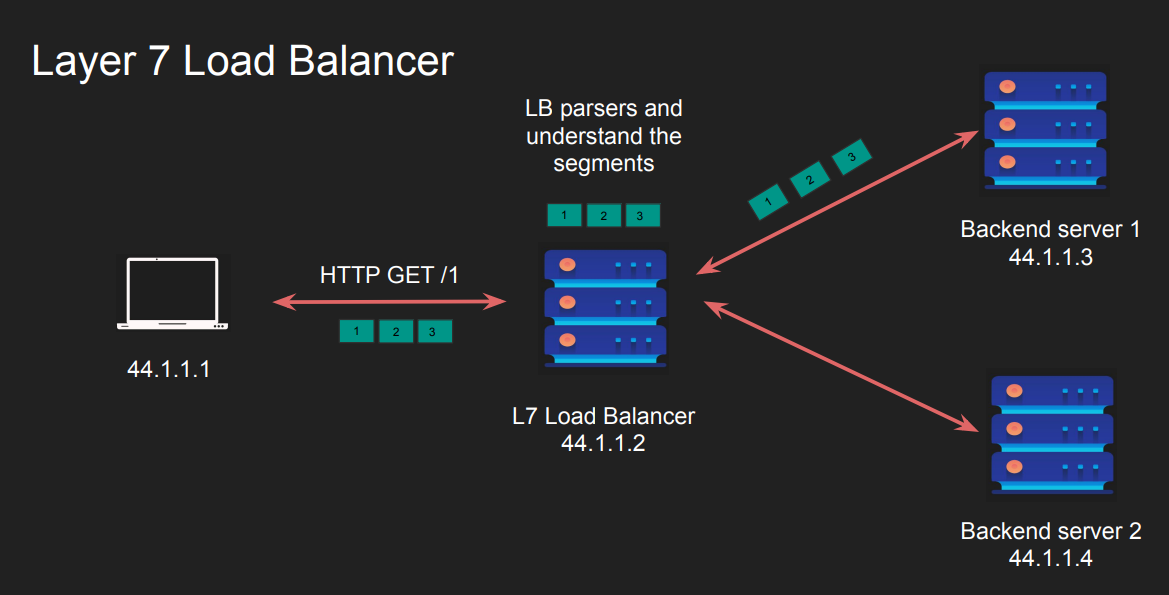
-
Content Inspection:
- When a client sends a request (e.g., visiting a webpage or calling an API), the Layer 7 load balancer reads the content of the request.
- It analyzes details like:
- URL paths:
/images,/videos,/api/users - HTTP methods:
GET,POST,PUT,DELETE - Headers: User-Agent, Cookies, Content-Type, etc.
- Payload: For example, JSON data in an API call.
- URL paths:
-
Routing Decisions:
- Based on this inspection, the load balancer determines the most appropriate backend server for the request.
- Example Routing Scenarios:
- Requests to
/imagesare sent to a server optimized for static content. - API calls to
/api/usersare routed to a backend microservice managing user data. - Requests with specific headers (e.g., mobile device identifiers) are sent to a dedicated server for mobile clients.
- Requests to
-
TLS Termination:
- For HTTPS requests, the load balancer decrypts the request to inspect its contents, a process called TLS termination.
- To do this, the load balancer requires access to the server’s SSL/TLS certificate.
-
Response Handling:
- The backend server processes the request and sends a response to the load balancer, which forwards it to the client.
Pros of Layer 7 Load Balancers
-
Smart Routing:
- Layer 7 load balancers can make content-based decisions, ensuring requests are handled by the most appropriate server.
- Example: A news website routes video requests to a media server and article requests to a text-optimized server.
-
Caching:
- Frequently accessed content (e.g., images, static files, or popular API responses) can be cached by the load balancer.
- This reduces the load on backend servers and improves response times for users.
-
Support for Microservices:
- Layer 7 load balancers can route requests to specific microservices based on paths or headers.
- Example:
/ordersgoes to an order management microservice, while/productsgoes to an inventory service.
-
Enhanced Security Features:
- They can filter malicious traffic by inspecting content for threats (e.g., SQL injection or cross-site scripting attacks).
- They can enforce authentication and authorization rules at the load balancer level.
Cons of Layer 7 Load Balancers
-
Performance Overhead:
- Since the load balancer inspects, decrypts, and processes content, it uses more CPU and memory than Layer 4 load balancers.
- This can lead to slower response times if not properly scaled.
-
Resource-Intensive:
- TLS termination requires the load balancer to handle encryption and decryption, adding computational overhead.
- Content inspection and routing logic consume additional resources.
-
Protocol-Specific:
- Layer 7 load balancers must understand the protocol being used (e.g., HTTP, gRPC).
- Supporting a new protocol may require updates or additional configuration.
-
Complex Configuration:
- Setting up and maintaining rules for content-based routing can be more complicated compared to simpler Layer 4 load balancing.
Example Use Case for Layer 7 Load Balancer
E-commerce Website:
- Routing Example:
- Static Content: Requests for images, CSS, or JavaScript files are routed to a CDN or caching server.
- APIs: Requests to
/cartor/checkoutare sent to dedicated microservices for handling shopping carts and payment processing. - Dynamic Pages: User-specific pages like
/profileare sent to application servers that query databases.
When to Choose Layer 7 Load Balancers
- For Intelligent Routing: If your application requires routing based on URLs, headers, or other request details.
- For Caching: If your site serves a lot of static or frequently accessed content.
- For Microservices: If your backend consists of multiple services handling specific tasks.
- For Enhanced Security: If you need to filter requests or enforce authentication at the load balancer level.
Layer 7 load balancers excel in complex environments where content-specific routing and advanced features are necessary. They are ideal for modern applications built on microservices or serving diverse types of content. However, their increased resource requirements and complexity mean they should be used thoughtfully, especially for high-traffic systems.
Comparing Proxy, Reverse Proxy, and Load Balancers
| Feature | Proxy | Reverse Proxy | Load Balancer (Layer 4) | Load Balancer (Layer 7) |
|---|---|---|---|---|
| Who It Helps | Clients | Servers | Servers | Servers |
| What It Hides | Client’s identity | Server’s identity | Server’s identity | Server’s identity |
| Decision Making | Basic forwarding | Basic routing | Simple traffic sharing | Content-based routing |
| Speed | Fast | Moderate | Fast | Moderate |